How message authentication code works?
Apart from intruders, the transfer of message between two people also faces other external problems like noise, which may alter the original message constructed by the sender. To ensure that the message is not altered there’s this cool method MAC.
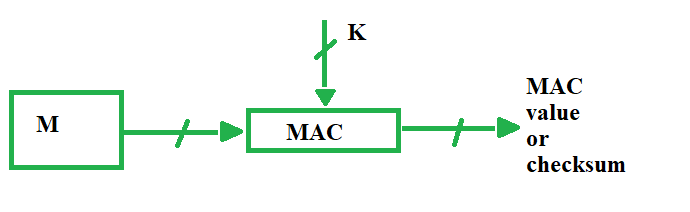
MAC stands for Message Authentication Code. Here in MAC, sender and receiver share same key where sender generates a fixed size output called Cryptographic checksum or Message Authentication code and appends it to the original message. On receiver’s side, receiver also generates the code and compares it with what he/she received thus ensuring the originality of the message. These are components:
- Message
- Key
- MAC algorithm
- MAC value
There are different types of models Of Message Authentication Code (MAC) as following below:
- MAC without encryption –
This model can provide authentication but not confidentiality as anyone can see the message.
- Internal Error Code –
In this model of MAC, sender encrypts the content before sending it through network for confidentiality. Thus this model provides confidentiality as well as authentication.M' = MAC(M, k)
- External Error Code –
For cases when there is an alteration in message, we decrypt it for waste, to overcome that problem, we opt for external error code. Here we first apply MAC on the encrypted message ‘c’ and compare it with received MAC value on the receiver’s side and then decrypt ‘c’ if they both are same, else we simply discard the content received. Thus it saves time.c = E(M, k') M' = MAC(c, k)
Problems in MAC –
If we do reverse engineering we can reach plain text or even the key. Here we have mapped input to output, to overcome this we move on to hash functions which are “One way”.
Note – symbol “E” denotes symmetric key encryption.
Join the conversation